Remote work and hybrid models have become a reality for many companies, providing flexibility to employees and optimizing resources for organizations. However, allowing remote access to the corporate network entails new challenges in cybersecurityCybersecurity solutions are essential in this era.. In this context, Zero Trust Network Access (ZTNA) stands out as an advanced solution to ensure secure connections without compromising the integrity of business systems.
What is ZTNA and how does it protect corporate network access?
Zero Trust Network Access (ZTNA) is a technology based on the Zero Trust model, which is founded on the premise that no user or device should be considered trustworthy by default. Unlike traditional security models that assumed any user within the corporate network was safe, ZTNA constantly verifies the identity and context of each access attempt.
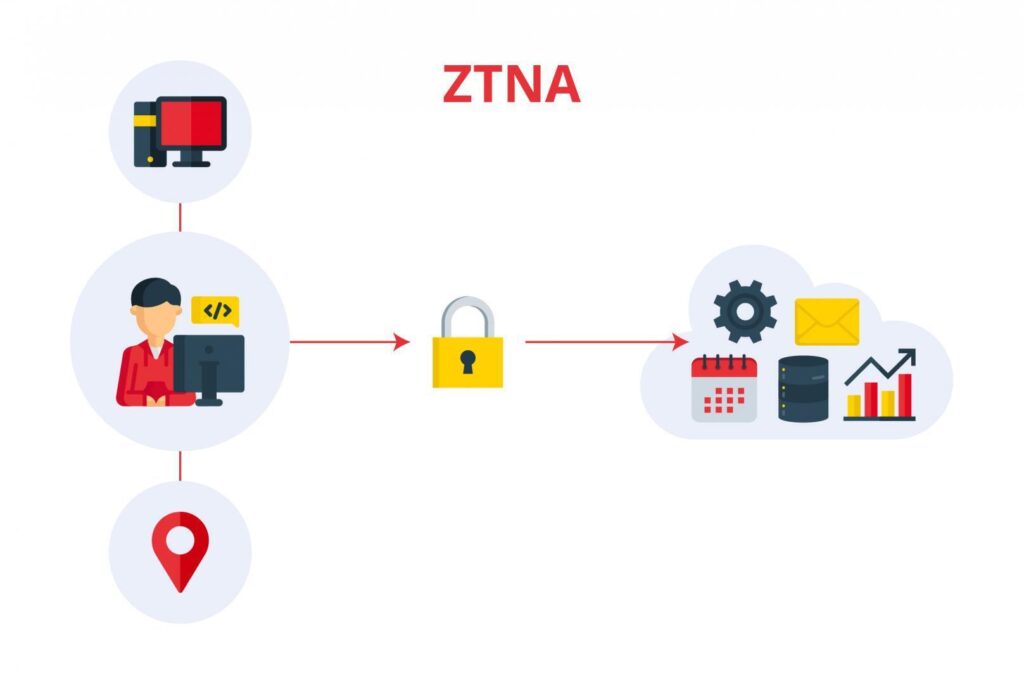
To achieve this, ZTNA employs mechanisms such as multi-factor authentication and analyzes various criteria, including:
- User identity
- Access location and time
- Device used
With this methodology, unauthorized actors are prevented from accessing critical business resources, minimizing the risk of security breaches.
ZTNA vs. VPNA VPN, short for Virtual Private Network, provides a secure: why is it a more secure alternative?
Many companies have used VPNs (virtual private networks) to enable remote access to their corporate networks. However, ZTNA surpasses VPNs in terms of security and scalability, especially in hybrid or cloud work environments. Some key differences include:
🔒 Segmented and granular access: While a VPN allows general access to the entire network, ZTNA only grants access to strictly necessary resources for each user.
🛡️ Greater security at the application layer: ZTNA protects individual applications rather than granting global access to the network, reducing the attack surface.
📈 Scalability and flexibility: VPNs can become challenging to manage as the company grows. In contrast, ZTNA dynamically adapts to the expansion of resources and users.
🔄 Continuous verification: While a VPN only validates identity at the time of connection, ZTNA performs constant checks, enhancing protection against unauthorized access.
Benefits of ZTNA for businesses
Implementing ZTNA in an organization offers multiple advantages in terms of security and operational efficiency:
✅ Reduction of unauthorized access risks: By applying the “zero trust” philosophy, ZTNA minimizes the impact of potential cyberattacks.
✅ Secure access from any location: Ideal for remote or hybrid work models, allowing protected connections to business systems from anywhere in the world.
✅ Segmentation and access control: Each user can only access the resources they truly need, avoiding unnecessary exposures and facilitating permission management.
✅ Less vulnerability to attacks: By restricting general access to the network and limiting it to essential applications, exposure to potential cyberattacks is reduced.
✅ Regulatory compliance: ZTNA facilitates compliance with regulations such as GDPR and LOPDGDD, ensuring more precise control over access to sensitive data.
ZTNA: a key solution for business cybersecurity
In an environment where cybersecurity is a priority, ZTNA positions itself as an advanced solution to protect access to companies’ digital resources. Its approach based on continuous verification and segmented access provides a higher level of security than VPNs, better adapting to the needs of remote work and digital transformation.
Companies looking to enhance their cybersecurity strategy can greatly benefit from this technology, protecting their infrastructure without sacrificing the flexibility and productivity of their teams.
via: INCIBE

