A security researcher discovered a vulnerability in the content delivery network (CDNA CDN, short for Content Delivery Network…) of Cloudflare, which could allow attackers to determine a user’s approximate geographic location simply by sending them an image through messaging apps like Signal and Discord.
How the Attack Works
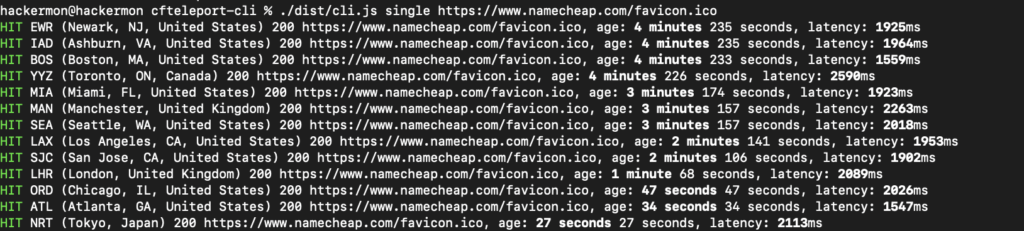
The flaw, discovered by a researcher named Daniel, exploits the mechanism of Cloudflare Workers, which caches multimedia resources at the data centerA data center, or data processing center… closest to the user to improve loading times. The attack involves sending a message with a unique image hosted on Cloudflare’s CDN. By using a custom tool named Cloudflare Teleport, the attacker can force requests to go through specific data centers, thereby mapping the user’s approximate location.
The detected location varies from 50 to 300 miles from the actual place, depending on proximity to Cloudflare’s data centers. This attack is especially effective in urban areas where there are multiple data centers, increasing accuracy.
A “Zero-Click” Attack
What makes this attack concerning is that it does not require user interaction. Many applications like Signal and Discord automatically download images for push notifications, allowing the attacker to obtain the user’s location without them even noticing.
The accuracy of this attack varies by region, being more precise in large cities and less reliable in rural areas. During his tests, Daniel demonstrated that he could successfully track Discord’s CTO, Stanislav Vishnevskiy, using this technique.
Response from Affected Platforms
The researcher reported his findings to Cloudflare, Signal, and Discord. Cloudflare acknowledged the issue and released a fix for the bug in Workers, granting a reward of $200 to the researcher. However, Daniel noted that by using a VPNA VPN, short for Virtual Private Network… with globally distributed servers, he can still access more than 50% of Cloudflare’s data centers, indicating that the vulnerability is not completely mitigated.
Signal and Discord denied direct responsibility for the issue. Signal argued that network-level anonymization falls outside the scope of its mission, while Discord stated that the problem lies with Cloudflare’s infrastructure.
Risks and Recommendations
While this attack is not precise enough to pinpoint specific addresses, it does allow for the identification of geographical regions and movement patterns. This is especially concerning for users with higher privacy needs, such as journalists, activists, or dissenters.
Recommendations for users and administrators:
- Disable content caching in sensitive applications.
- Limit automatic image downloading in messaging apps.
- Avoid using applications that do not implement security measures in their network services.
This finding underscores the importance of ongoing vigilance in the security of CDNs and how cloud services handle their users’ data.
via: Bleeping Computer

