The ransomware landscape continues to evolve with concerning trends affecting key sectors and exposing critical vulnerabilities. According to the latest report from Halcyon’s threat research team, based on intelligence gathered in December 2024, the sophistication and scope of ransomware attacks continue to grow.
Most Affected Sectors
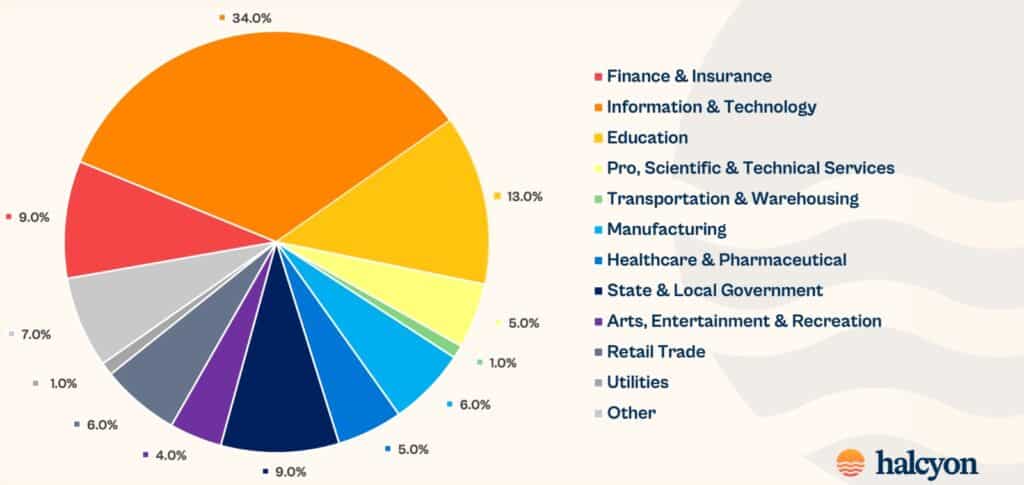
In December 2024, the sectors most affected by ransomware were as follows:
- Information Technology (IT): 34% (+6% month-over-month).
- Education: 13% (unchanged).
- Finance and Insurance: 9% (-4%).
- State and Local Governments: 9% (+1%).
- Other Sectors: 7% (+6%).
- Manufacturing: 6% (-7%).
- Retail: 6% (+3%).
- Healthcare and Pharmaceuticals: 5% (unchanged).
- Professional, Scientific, and Technical Services: 5% (+2%).
- Arts, Entertainment, and Recreation: 4% (-4%).
These figures highlight that critical sectors such as IT, education, and finance remain prime targets for cybercriminals, presenting significant challenges for infrastructure and data security.
Tools and Techniques Used
The report highlights that threat actors are using advanced tools as precursors to ransomware attacks. These tools include:
- Hacktool.EdRSilencer/EDRStealer: Designed to disable endpoint detection and response (EDR) solutions, facilitating malicious activities without detection.
- Hacktool.Lazagne/Clyp: A credential thief that extracts sensitive information, such as passwords and authentication tokens.
- Hacktool.MailBruter: A tool for compromising email accounts through brute-force attacks.
- Hacktool.sharphound/msil: Used to map Active Directory environments, allowing lateral movement and privilege escalation.
Major Ransomware Families Detected
Among the ransomware payloads blocked by Halcyon are:
- LockBit/Fragtor: Known for its rapid encryption and advanced evasion capabilities.
- Phobos/Zusy: An adaptable ransomware with data theft capabilities.
- LockBit/BlackMatter: Combines features from the LockBit and BlackMatter families, employing double extortion tactics.
- Akira/Dacic: Notable for disabling security tools and encrypting critical data.
- Incransom/Imps: Uses double extortion by exfiltrating data before encrypting it.
Focus on Double Extortion
Most modern ransomware variants now employ double extortion tactics. This involves not only encrypting data but also threatening to publish stolen information if victims do not pay the ransom. This strategy increases pressure on affected organizations, exposing them to financial and reputational risks.
Projections for 2025
The report notes that a resurgence of advanced threats like LockBit 4.0 is expected, with its launch scheduled for February 2025. Furthermore, groups like Cl0p have intensified their exploitation campaigns, highlighting the need for constant vigilance.
Recommended Protective Measures
To mitigate risks, Halcyon advises:
- Implement proactive strategies: Including network segmentation and strict privilege management.
- Continuously monitor: Adopt advanced detection and response solutions.
- Train employees: To identify phishing attempts and minimize human error.
- Regularly back up data: With copies stored offline.
The dynamic nature of ransomware underscores the importance of a comprehensive cybersecurityCybersecurity solutions are essential in the era of… strategy to protect organizations from the escalating threats in 2025.
via: Halcyon

