Q3 2025 confirms what many security teams have suspected for months: the scale and speed of distributed denial-of-service (DDoS) attacks have entered a new era. Cloudflare has just published its quarterly DDoS threat report, with the main focus being Aisuru, a massive botnet that has propelled hyper-volume attacks to unprecedented levels.
According to data collected across its global network, the company automatically mitigated 8.3 million DDoS attacks between July and September, representing a 15% quarter-over-quarter increase and a 40% year-over-year increase. Year-to-date 2025, the total so far amounts to 36.2 million attacks blocked, which is 170% of all attacks mitigated in 2024, with one quarter remaining in the year.
In practical terms, this means Cloudflare was stopping an average of 3,780 DDoS attacks every hour during the quarter. In other words, dozens of attempts to take down critical services every minute somewhere on the planet.
Aisuru, the botnet that redefines the “peak” of an attack
In this already volatile landscape, Aisuru is the piece that disrupts the entire game. Cloudflare describes this botnet as an “army” of between 1 and 4 million compromised devices distributed worldwide. Its specialty is hyper-volume attacks, with peaks easily exceeding 1 terabit per second (Tbps) and 1 billion packets per second (Bpps).
In Q3, the number of these massive attacks surged by 54% compared to the previous quarter, reaching an average of 14 hyper-volume attacks per day. Among these, two were particularly noteworthy:
- An attack of 29.7 Tbps, which Cloudflare qualifies as a world record.
- An attack of 14.1 Bpps, another record high in packets per second.
Regarding the 29.7 Tbps attack, it was a UDP carpet-bombing attack, sending traffic simultaneously to about 15,000 destination ports per second. The distributed traffic and packet attribute randomization aimed to evade filtering systems, but Cloudflare’s automated defenses detected and mitigated the onslaught without human intervention.
Since early 2025, the company has neutralized 2,867 attacks attributable to Aisuru, of which 1,304 occurred this third quarter.
Larger attacks… and increasingly shorter
Size isn’t the only issue. The report emphasizes that attacks are shorter and more explosive, further complicating responses.
- Attacks exceeding 100 million packets per second (Mpps) increased by 189% quarter-over-quarter.
- Those surpassing 1 Tbps grew by 227% in the same period.
- At the HTTP layer, 4 out of 100 attacks exceeded 1 million requests per second.
At the same time, 71% of HTTP attacks and 89% of network attacks last less than 10 minutes. Many are active for just seconds, but the operational impact can last hours: restoring data consistency in distributed systems, rebuilding sessions, verifying the absence of corruption, and returning services to normal for users.

This “lightning strike” pattern renders traditional approaches—such as calling on on-demand cleaning services or manually activating firewall rules—completely inadequate. By the time engineering teams react, the attack has often ended… and the service remains down.
The weight of L3/L4: most attacks focus on the network
In Q3 2025, 71% of observed DDoS attacks were layer 3/4 (network layer), compared to a 29% HTTP attacks. In absolute numbers, this accounts for about 5.9 million network attacks and 2.4 million HTTP attacks.
Trends also diverge:
- Network attacks increased by 87% quarter-over-quarter and 95% year-over-year.
- HTTP attacks, however, fell 41% compared to the previous quarter and 17% compared to the same period in 2024.
The explanation is largely tied to Aisuru’s push, which favors volumetric network vectors, especially UDP floods, which have skyrocketed by 231% quarter-over-quarter and become the most common vector. Following them are DNS attacks, SYN floods, and ICMP floods, collectively making up just over half of all network DDoS attacks.
Despite nearly a decade since their first major appearance, the report confirms that Mirai remains highly present: about 2 out of every 100 network attacks still originate from variants of this historic botnet.
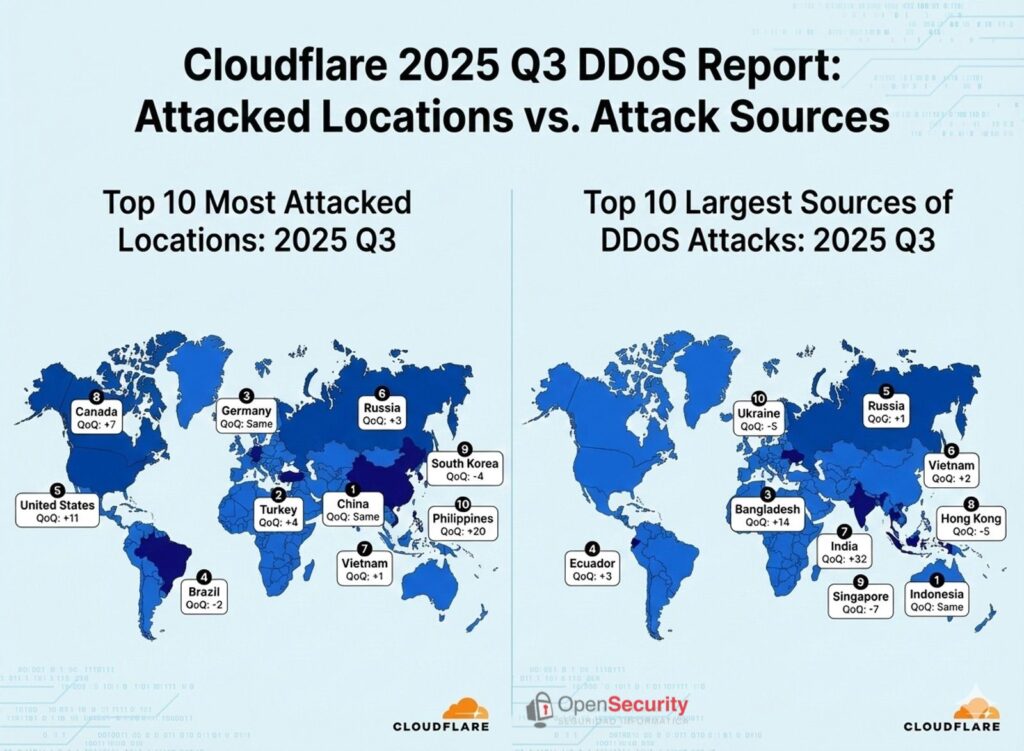
Indonesia, the epicenter of malicious traffic
Regarding the origin of DDoS traffic, the map again points to Asia as a key region. Seven of the top ten attack sources are located in this continent, with Indonesia leading.
Indonesia has been the leading country of origin for DDoS attacks for an entire year. The trend is striking: in just five years, since Q3 2021, the percentage of HTTP DDoS requests originating there has increased by 31,900%, according to Cloudflare data.
The company notes that “origin” does not necessarily mean attribution: many of these requests come from compromised devices or misconfigured services in those countries, not necessarily local malicious actors.
From rare earths to cars: industries in the spotlight
Cloudflare’s report confirms that attackers are choosing their targets aligned closely with economic and geopolitical agendas.
In the Mining, Minerals, and Metals sector, DDoS attacks increased notably during the third quarter, paralleling escalating tensions between the European Union and China over electric vehicle tariffs, rare earth exports, and cybersecurity requirements. This sector rose 24 places in the global ranking to rank 49th among the most attacked industries.
The Automotive industry saw the most dramatic jump, climbing 62 positions in just one quarter to become the sixth most attacked sector globally. Cybersecurity companies also experienced a significant increase in attacks, moving up 17 places to rank 13th.
Overall, the most attacked sectors in the quarter were:
- Information Technology and Services
- Telecommunications
- Online gaming and casinos
Followed by Banking and Financial Services, Retail, Consumer Electronics, and the mentioned Automotive and Media/Publishing sectors, all of which saw notable surges.
AI companies, primary targets: peaks up to 347% in September
One of the most impactful data points directly affects the generative AI ecosystem. In September 2025, amid a month packed with headlines on regulation, ethics, and AI use in governments, Cloudflare detected monthly increases of up to 347% in HTTP DDoS attack traffic targeting AI companies, based on several leading sector services.
That same month, a survey by the Tony Blair Institute showed that a significant portion of the British public perceives AI more as an economic risk than an opportunity, while the UK’s Law Commission announced a review of AI use in public administration. Parallel to societal debates, systems hosting AI models in the cloud became an obvious target.
For startups and model providers, this trend presents a double challenge: defending APIs and management dashboards against application attacks and securing network infrastructure against massive campaigns designed to saturate bandwidth and computing resources.
When protests go digital: Maldives, France, Belgium
Cloudflare continues to observe a direct correlation between street protests and DDoS attacks.
- In Maldives, protests under the slogan “Lootuvaifi” (“Stop the Loot!”) against perceived corruption and a controversial media law coincided with a wave of DDoS attacks. The country climbed 125 places in the ranking to become the 38th most attacked in the world.
- In France, the “Block Everything” movement, led by unions protesting austerity, pension changes, and rising costs, was accompanied by attacks on French websites and services. France rose 65 places to become the 18th most attacked country.
- In Belgium, demonstrations marking the “red line” for Gaza in Brussels also coincided with increased attacks, moving the country up 63 places to position 74.
Among the top 10 most attacked countries, China remains first, followed by Turkey and Germany. The United States experienced one of the biggest jumps, moving up 11 positions to fifth place, while Philippines rose 20 spots to also enter the top ten.
HTTP DDoS: known botnets, fake browsers, and login attacks
At the HTTP layer, Cloudflare notes that almost 70% of DDoS attacks originate from botnets already identified in its radar. This illustrates one of the benefits of operating a global network: once a botnet targets a client, signatures and patterns are shared automatically to protect others.
Another roughly 20% of HTTP attacks come from fake or headless browsers or from requests with suspicious attributes. The remaining 10% is divided between generic floods, cache-busting requests, and attacks targeting login pages, where high volumes of simultaneous requests can block legitimate user access.
Why legacy DDoS defenses fall short
Cloudflare’s conclusion is clear: The combination of larger, faster attacks aligned with political and economic events makes many traditional defense strategies obsolete.
Organizations relying on:
- On-premise appliances with limited traffic capacity.
- On-demand scrubbing services requiring manual activation or scaling.
are at a disadvantage against attacks that last seconds but saturate lines of several Tbps. When an attack causes “collateral damage” to ISPs’ infrastructure—not even the intended target—there is no human window to react.
In this context, the report advocates for always-on, autonomous mitigation, integrated into a global network-as-a-service. Cloudflare reminds that it offers unlimited-volume DDoS protection with no extra charges for attacks to all customers, as part of its “connectivity cloud” offering, combining enterprise network protection, application acceleration, and Zero Trust controls in a unified platform.
Frequently Asked Questions about Cloudflare’s DDoS report and the Aisuru botnet
What exactly is Aisuru, and why is it such a concern for cybersecurity experts?
Aisuru is a massive botnet, with between 1 and 4 million compromised devices worldwide, capable of launching hyper-volume DDoS attacks exceeding 29.7 Tbps and 14.1 Bpps. Its size, the availability of “botnet slices” as a rental service, and its ability to cause collateral damage even beyond its direct targets make it one of the most serious threats today.
Why are so many DDoS attacks so short if their impact can last for hours?
Attackers favor brief campaigns—often under 10 minutes—to maximize surprise and minimize the chance of manual response. Although the attack only lasts seconds, it can desynchronize databases, break user sessions, and destabilize critical systems, leading to long recovery and verification processes by technical teams.
Which sectors and countries should be most concerned about the rise in DDoS attacks in 2025?
The most targeted sectors include information technology, telecommunications, online gaming, banking, retail, automotive, cybersecurity, and media. Geographically, China, Turkey, Germany, the US, and the Philippines rank among the hardest hit. Maldives, France, and Belgium have experienced sharp increases linked to protests and internal political tensions.
What can companies do to defend themselves against Aisuru and hyper-volume DDoS attacks?
Experts recommend re-evaluating strategies relying solely on local appliances or on-demand services and adopting always-on protective measures capable of automatically mitigating hyper-volume attacks within seconds, near the traffic source. Integrating such protection into a secure connectivity architecture—alongside CDN, WAF, and Zero Trust—helps reduce risks at both network and application layers.
Sources:
Cloudflare – Cloudflare’s 2025 Q3 DDoS Threat Report – including Aisuru, the apex of botnets
Cloudflare – DDoS reports and attack trends in 2025

