Monday, November 18, 2025 (midday in Spain) kicked off with a jolt for a large part of the internet: Cloudflare, one of the world’s major CDN, DNS, and web security providers, is experiencing an outage in its global network, causing widespread 500 errors and making both the control panel and the API unresponsive.
According to the company’s own status page, the issue results in “widespread 500 errors” affecting multiple clients, while the dashboard and API are also failing or responding intermittently. The incident is classified as “Cloudflare Global Network experiencing issues” and, for now, is under internal investigation.
What is known so far about Cloudflare’s outage
Based on the information published by the company, the timeline of the incident is as follows (times in UTC):
- 11:48 UTC – Cloudflare acknowledges awareness of a problem causing 500 errors and failures in both the dashboard and API, and states that it is investigating the impact on clients.
- 12:03 UTC – The company updates the situation report, confirming that it continues analyzing the root cause and precise scope of the incident, without yet providing a technical diagnosis or estimated resolution time.
Meanwhile, the status page reports scheduled maintenance work at various data centers (Santiago de Chile –SCL–, Tahiti –PPT–, Los Angeles –LAX–, and Atlanta –ATL–) at different times throughout the day. These maintenance activities typically involve traffic reroutes to other network points and normally cause only temporary latency increases.
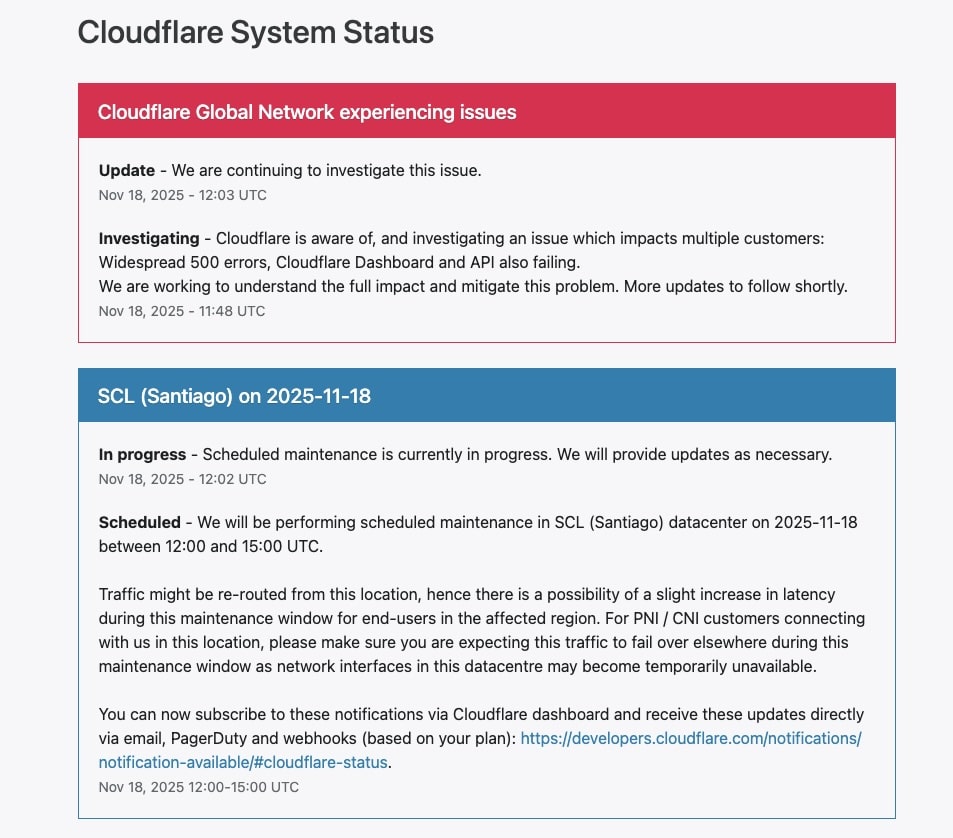
At this stage, Cloudflare has not officially linked these maintenance activities to the global network outage, so they should be considered separate events until the company indicates otherwise.
Why an outage at Cloudflare affects the entire internet
Cloudflare is one of the key invisible cogs of the internet:
- It acts as a content delivery network (CDN),
- Offers managed DNS services,
- Protects sites and APIs with web application firewall (WAF) and DDoS mitigation,
- And functions as an intermediary layer between end users and origin servers.
When that “intermediary layer” fails, the visible symptom for users is usually the same: websites won’t load, APIs return errors, or admin panels stop responding. For many companies, this happens even if their origin servers are functioning correctly—the bottleneck is at the intermediary provider.
In an ecosystem where millions of websites, online stores, SaaS services, and mobile apps depend on Cloudflare to accelerate and secure traffic, an incident like this quickly becomes a global problem.
What do the 500 errors seen by users mean?
Cloudflare’s reports mention “widespread 500 errors”. The 500 status code is a generic HTTP error indicating a “Internal Server Error”: something on the server side failed before it could deliver a valid response to the browser or app.
Within Cloudflare’s context, 5xx errors can originate from:
- Failures or overloads in the client’s origin servers,
- Internal issues within Cloudflare’s infrastructure,
- Intermediate configuration errors (such as rules, routing, or load balancing),
- Or a combination of several factors.
Cloudflare’s technical documentation states that 5xx errors are usually related to failures at the server or infrastructure level that serves requests, whether the origin host or the edge network.
In this specific case, considering the reports of widespread 500 errors across the global network and simultaneous failures of both dashboard and API, everything points to a problem within Cloudflare’s platform itself, rather than an isolated failure of client servers. However, we’ll need to wait for the official report to understand the root cause.
Impact on companies and end users
The actual impact of an outage like this depends on how each organization uses Cloudflare, but the most common effects include:
- Unreachable or very slow websites and online stores, leading to sales loss during the incident.
- Downed admin dashboards and APIs, complicating rule, DNS, certificates, or monitoring management.
- Affected internal or B2B services, especially when APIs and mobile apps rely on Cloudflare as an entry point.
- Increased latency or timeouts as traffic is rerouted to other network points under stress.
This kind of episode underscores once again the dependence on a small number of infrastructure providers. Although Cloudflare promotes a distributed, highly resilient architecture, even robust platforms can suffer failures that are amplified by the massive traffic they handle.
What IT teams can do now
While Cloudflare works to resolve the incident, some cautious measures technical teams can take include:
- Check origin server status (own servers, databases, etc.) to ensure the issue isn’t just on Cloudflare’s side or internal infrastructure.
- Avoid drastic configuration changes during the incident (DNS, origin migration, bulk rule updates), to prevent adding variables to the problem.
- Maintain clear communication with business and clients, explaining that it’s an issue with an external provider and that it’s being monitored in real time.
- Review future contingency plans, including alternative DNS routes or configurations that can bypass the CDN/security layer temporarily if risk allows.
A reminder of the fragility of digital infrastructure
Although it’s still early to draw definitive conclusions, today’s outage reinforces that resilience depends not only on internal enterprise design but also on decisions about where to entrust critical connectivity and security layers.
When a single provider handles a significant portion of global web traffic, any failure results in a sort of “mini internet blackout” for millions. The good news is that Cloudflare generally reacts quickly and releases post-incident reports; the bad news is that these kinds of interruptions are likely to keep happening as infrastructure complexity continues to grow.
For now, the clear recommendation is: keep an eye on Cloudflare’s official status page, avoid sudden changes, and have contingency plans ready for when the intermediary network layer goes down at the worst moment.
via: Cloudflare status

