The free software used in VMware environments has been exploited as bait by malicious actors to distribute malware from fraudulent websites and even from its own official domain.
RVTools, one of the most popular utilities among administrators of VMware environments, has been the target of a cyberattack campaign that includes the distribution of malicious installers through spoofed sites and even through a compromised official website for several hours.
A modified installer, same appearance… and included malware
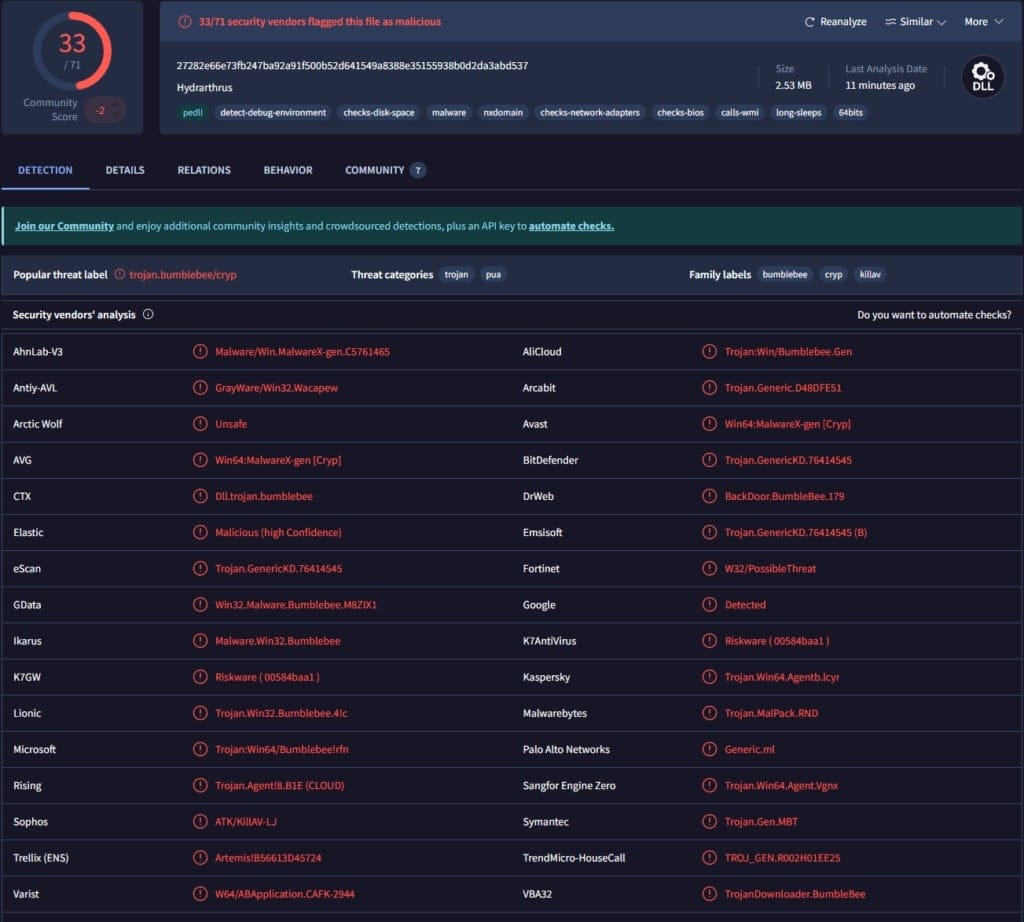
On May 13, 2025, security researcher Aidan Leon raised the alarm after detecting a high-confidence alert generated by Microsoft Defender for Endpoint. An employee at his company attempted to install RVTools from the official site, but the installer contained a suspicious file —version.dll— which turned out to be a Bumblebee malware loader, commonly used to deploy ransomware and post-exploitation tools.
According to the analysis, the malicious installer was uploaded to the official Robware.net site on Monday, May 12, between 8:00 and 11:00 AM, and was accessible until Tuesday afternoon. During that time, the page served a file larger than usual, whose hash did not match the legitimate version. By 3:00 PM on Tuesday, the installer was replaced with a clean version, and the site briefly became available again before going down once more.
Dell responds: no confirmed compromise, but attacks occurred
Dell Technologies, the current steward of the software, has denied that its domains were compromised. In a statement, the company claims that “our Robware.net and RVTools.com sites were subject to denial of service (DOS) attacks, and were disabled as a precautionary measure.” They also confirmed the detection of multiple fraudulent sites designed to mimic the official portals and distribute malware.
Currently, both sites remain offline, further complicating safe access to the tool for system administrators. The situation has created confusion, especially as fraudulent domains like rvtools[.]org appear in the top search results on Google without being sponsored ads.
Potential damages and attack targets
The distributed malware is designed to steal:
- Credentials and passwords
- Data stored in browsers
- Cryptocurrency wallets
- Sensitive system files
The infected file is typically presented in a compressed format (.ZIP), and when executed by the user, it installs RVTools along with the malware, without the user suspecting anything unusual. This type of attack, based on social engineering and search result manipulation, is particularly dangerous as it targets professional environments where damage can escalate quickly.
Recommendations to avoid compromises
- ✅ Download only from verified sources: While the official site was briefly compromised in this case, it remains the main reference point. Always avoid sites that are not rvtools.com or robware.net.
- ✅ Check the file integrity: Compare the hash of your download with the one published in trusted repositories such as VirusTotal.
- ✅ Avoid sponsored results or suspicious domains in search engines.
- ✅ Always keep antivirus and operating systems updated.
Conclusion
This incident exposes a growing problem in the digital trust chain: even reputable tools can be used as an attack vector. In critical environments like managing virtualized infrastructures, verifying the authenticity of software and having robust security measures is not optional—it’s essential.
RVTools remains a useful tool, but until its official sites stabilize, extreme caution is recommended before any installation.
References: Zero day labs (img), Una al día, and Help net security