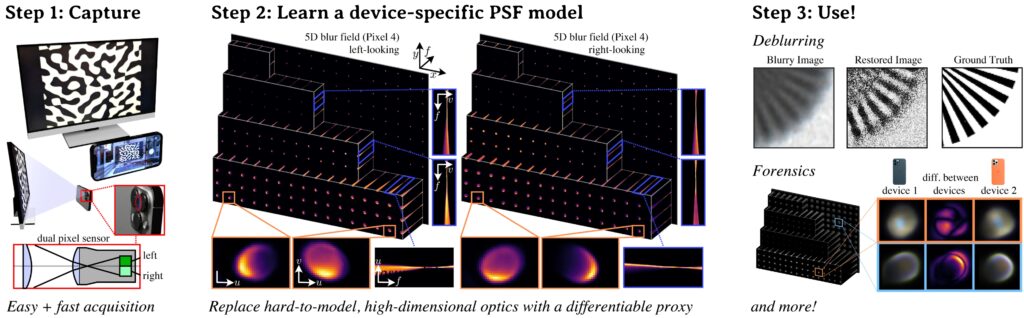
Until recently, anonymizing an image online seemed straightforward: just remove EXIF metadata and avoid displaying recognizable faces or locations. However, a new study reveals that this sense of anonymity could be an illusion. A team from the University of Toronto, MIT, and Adobe has developed a method to accurately identify which device took a photograph, even when two phones are the same model.
The key lies in the so-called Lens Blur Fields (LBF), an invisible pattern generated by each camera’s optical imperfections. These imperfections act like a unique digital fingerprint, similar to how rifling grooves in a bullet enable law enforcement to identify the gun used.
How this “digital ballistics” works
At the core of this breakthrough is a surprisingly simple process. Researchers found that it’s enough to:
- Display a calibration model on a monitor.
- Capture images over just five minutes.
- Process them with a multi-layer perceptron (MLP), a type of artificial neural network.
Using this system, they successfully distinguished photos taken by two different iPhone 12 Pro units, despite both being the same model. The explanation lies in the fact that each lens, even with minimal manufacturing variations, exhibits unique defects that influence defocus, aberrations, and diffraction.
These optical defects create a characteristic pattern—the LBF—that can be used to link an image to a specific device.
Applications: from forensic preservation to digital certification
The discovery opens up a range of legitimate applications:
- Forensics: authorities could determine whether a photo comes from a confiscated device in a criminal investigation.
- Digital authenticity: LBF could serve as an invisible watermark to verify an image’s origin, helping combat digital manipulation and misinformation.
- Editing and restoration: knowing a device’s optical signature would improve correction and deblurring algorithms tailored to each camera’s behavior.
The researchers also anticipate that the technique will work with DSLRs and mirrorless cameras, where interchangeable lenses have their own unique variations.
A clear privacy risk
While the previous applications seem positive, the scenario that this technology opens up in terms of privacy is concerning. The ability to associate anonymous photos with a specific device means that, even when metadata is removed, our visual anonymity could be compromised.
This raises several concerns:
- State surveillance: authoritarian governments could use this technique to trace the origins of uncomfortable images, such as protest photos or journalistic leaks.
- Risks for journalists and activists: reporters in conflict zones or human rights defenders could be identified and targeted through the images they share.
- Commercial exploitation: big tech platforms might use these invisible patterns as a more sophisticated way of digital tracking, linking accounts and profiles across services.
Researcher Esther Lin, one of the lead authors, warned on X (formerly Twitter) that the method is “surprisingly resistant to external factors” like dirt on the lens. While she acknowledged that filters or intensive editing could reduce its effectiveness, the reality is that the surveillance potential is already on the table.
Global surveillance: the dark side of progress
This discovery comes at a time when debates around digital privacy and mass surveillance are more intense than ever. The ability to link images to specific devices can be seen as a security advancement, but also as an unprecedented control tool.
In a world where citizens are already exposed to data mining, geolocation, and biometric identification, the possibility of tracking the authorship of any photo fuels fears of a Total Surveillance Ecosystem.
What might be useful for law enforcement could become a threat to freedom of expression and the right to anonymity—especially in countries where posting a critical image against those in power could result in legal repercussions… or worse.
An unvalidated technology
For now, the system’s code and the full dataset have not been published. The team plans to release a pioneering set of Lens Blur Fields data across five dimensions soon, which will allow others to reproduce and verify their results.
However, even without public validation, the fact that the technique was accepted in a prestigious journal like IEEE Transactions on Pattern Analysis and Machine Intelligence (TPAMI) suggests that it will be a hot topic of debate in the coming years.
Conclusion
The revelation that each camera leaves a unique optical fingerprint is a remarkable scientific breakthrough, with applications in security and digital authenticity. At the same time, it raises critical concerns regarding global privacy.
The challenge will be to find a balance: harnessing forensic and trust-enhancing benefits without turning technology into a tool for mass surveillance.
Ultimately, what might seem like a technical advance today could transform our understanding of freedom and privacy in the digital world tomorrow.
Frequently Asked Questions
Can this method identify any photograph?
Yes, as long as the image retains enough optical information. Aggressive processing or heavy compression can reduce accuracy but not eliminate it entirely.
Does the system only work with smartphones?
No. It’s also applicable to traditional digital cameras with interchangeable lenses, as they all have unique optical defects.
What are the privacy implications?
It could allow tracking the origin of anonymous images, even in sensitive contexts like protests or journalistic leaks, compromising user and activist anonymity.
Is this a real risk for global surveillance?
Potentially, yes. When combined with other identification technologies, LBF patterns could be used as an invisible layer of tracking in the digital age.
via: arXiv