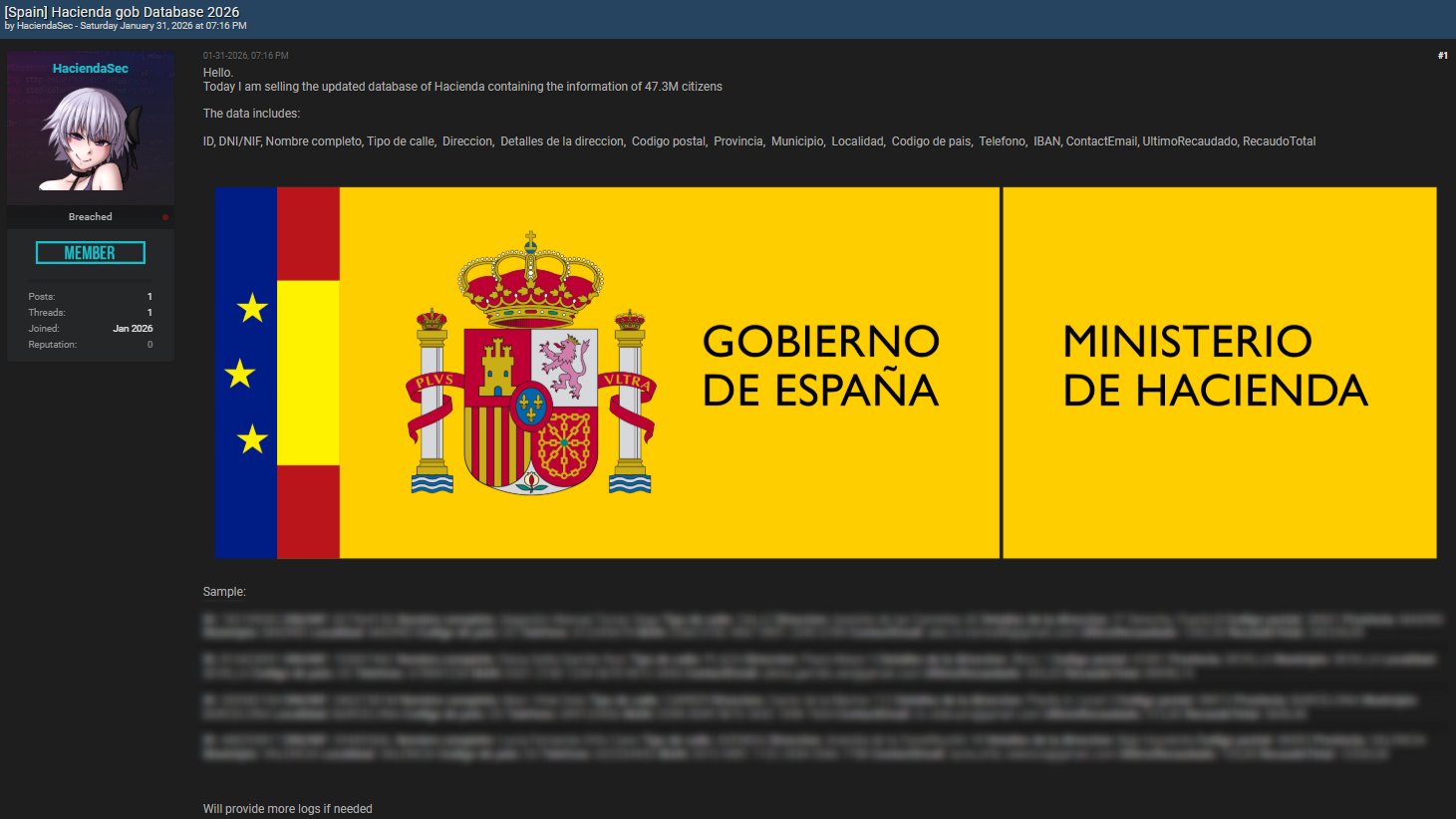
Spain wakes up to a new cybersecurity alarm signal on its radar. Several publications and specialized accounts have disseminated in recent hours the existence of a presumed unauthorized access to systems linked to the Ministry of Finance, attributed to an actor operating under the alias “HaciendaSec.” The claim — still awaiting independent verification — suggests that a “latest” database containing information on 47.3 million citizens is circulating or being offered for sale, including personal identifiers and, supposedly, financial and tax data.
What has been published and why is it relevant
The origin of the alarm is not an official statement but the echo of a chain that is quite common in high-impact incidents: a claim on forums and subsequent amplification through social media and digital media. In this case, the Hackmanac account (specialized in “early warning” of cyber risks) issued a notice attributing to the actor the offer of a database supposedly associated with Spanish citizens, with fields ranging from DNI/NIF to addresses, emails, phones, and bank references like IBAN, as well as tax information.
If confirmed, the volume would be extraordinary, but the real impact isn’t measured only in “quantity.” In cybersecurity, the combination of data (identity + contact + financial elements) multiplies the risk because it enables the design of more credible scams and impersonations compared to generic phishing.
The key nuance: there is currently no public confirmation of the incident
Unlike other cases where a breach is quickly verified through consistent samples or formal notification, here the scenario is more ambiguous. Some information indicates that the affected department itself is analyzing the veracity of the disseminated material and that, so far, no conclusive signs of intrusion have been observed, although the case is under review.
This point is crucial to prevent two equally damaging extremes: minimizing a serious possible incident or assuming a massive breach without verified evidence. Simultaneously, experience shows that even when a leak “comes from outside,” it can originate from third parties (suppliers, intermediaries, managers, integrators) or from reuse of data from previous sources, complicating attribution and response efforts.
What could happen if the data were real
In a scenario where the database is genuine or partially authentic, the main risks focus on four fronts:
- ID theft and banking fraud: with personal and banking data, the attacker doesn’t always need to “hack” into a bank; sometimes manipulating processes, deceiving support, or launching targeted scams suffice.
- Highly convincing phishing: emails or SMS messages containing full names, addresses, or tax references increase success rates. Users cease to see “just spam” and perceive “a real communication.”
- Extortion and doxxing: when contact and financial data are available, pressures and threats, especially toward public or business profiles, can emerge.
- Documentary fraud: from new service sign-ups to credit application requests or document duplicates, depending on the verification rigor required by each entity.
What citizens and businesses should monitor starting today
Although there is no official confirmation of a breach, the precautionary advice is to act as if there could be opportunistic campaigns (and this is almost certain): whenever news like this arises, many criminals use it as bait to deceive victims.
Useful measures, without causing alarm:
- Be cautious of messages requesting tax details, passwords, or codes via email/SMS, even if they cite “urgent” matters or “regularizations”.
- Do not click on links received through unsolicited channels; manually access official websites or use the usual app.
- Review bank transactions and activate alerts for charges if your bank offers this feature.
- Strengthen access security: use unique passwords and, where possible, two-factor authentication (especially for email, banking, and critical services).
- For businesses and law firms: reinforce anti-phishing filters, internal awareness, and verify “client” requests that arrive urgently or involve account changes.
The deeper debate: digital state, mass exposure, and trust
Beyond this particular case, the news highlights the ongoing structural issue of digital administration: the more centralized and valuable the databases, the higher the incentive to attack them — directly or indirectly — and the greater the potential impact. This requires sustained investment in monitoring, segmentation, access controls, audits, and incident response, along with communication capable of informing without inciting panic.
For now, the reasonable focus is on two questions: whether a breach truly occurred and, if so, where it originated (main system, subcontractor, provider, reuse of prior bases, etc.). Until these points are clarified, citizens remain in an uncomfortable zone: needing to protect themselves against a risk not officially confirmed but already exploited by the criminal ecosystem as bait.
Frequently Asked Questions
How can I tell if an email claiming to be from Hacienda is legitimate or a phishing attempt?
The most useful indicator is the method: if it asks for data, passwords, codes, or urgent payments via direct link, suspect. The safer practice is not to use the link and instead access through the official website (typed manually) or app.
What types of scams tend to increase after a suspected mass leak?
The scams typically include SMS with links, emails mimicking official notifications, and fake calls from supposed agents trying to obtain personal, banking, or verification codes.
Is it possible that the data sold is a mixture of old leaks and not direct access?
Yes. In many cases, actors recycle and “update” previous databases with information from various sources to sell a more attractive package. That’s why technical verification is key before confirming a breach.
What measures are most effective to protect against impersonation risks?
Activate bank alerts, strengthen passwords, enable two-factor authentication, and exercise extra caution with unsolicited communications. If fraud indications are detected, it’s advised to gather evidence and contact the affected entity as soon as possible.
Source: Presumed data leak from Hacienda