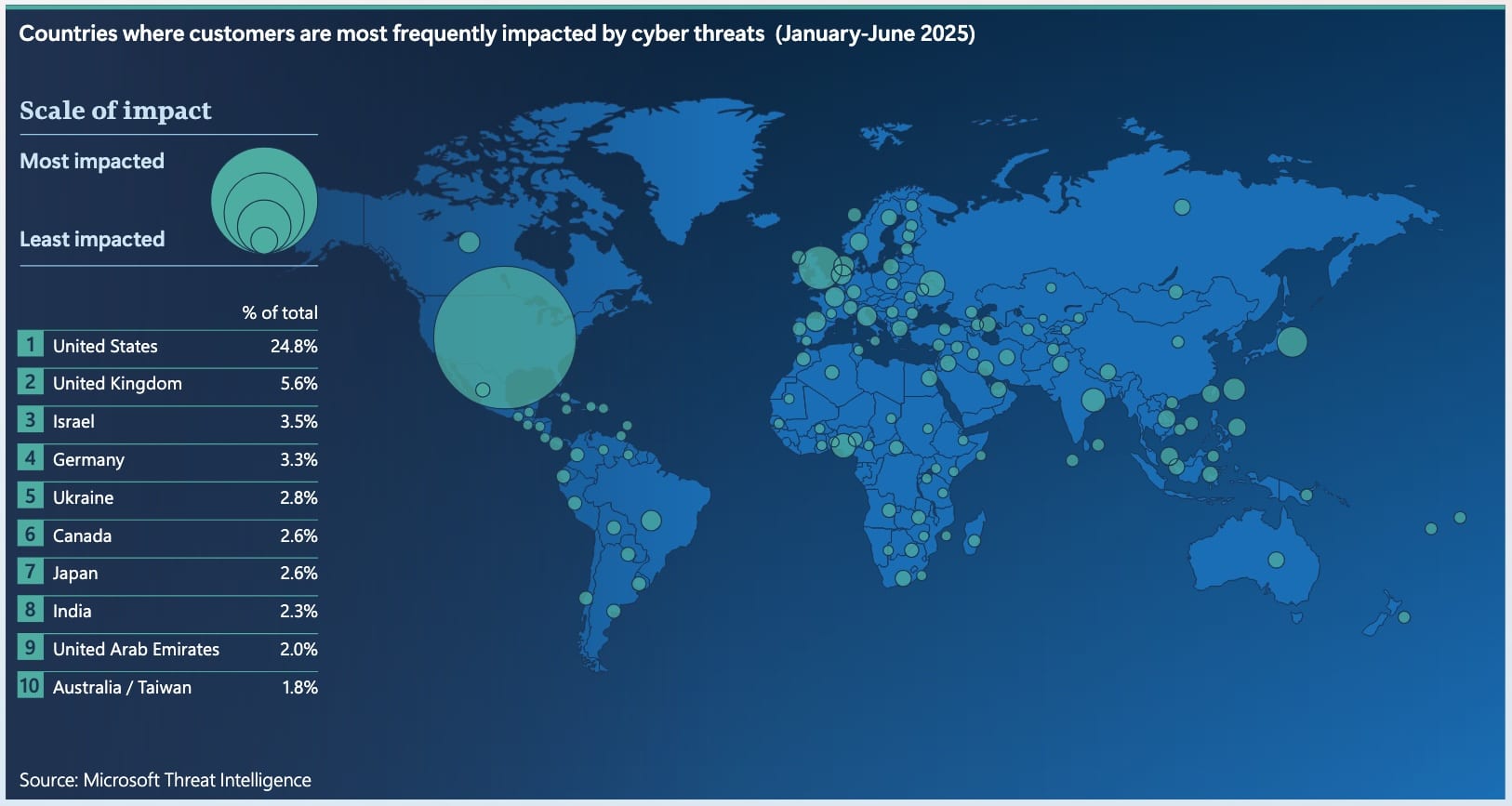
Spain ranked fifth in Europe for the frequency of cyberattacks on clients during the first half of 2025 and 14th global, according to the latest Microsoft report. During that period, approximately 5.4% of the affected clients in Europe were located in our country. The overall picture aligns with a clear technology and cloud trend: economic motivation dominates (extortion and ransomware), identity is the new perimeter, and AI accelerates both attacks and defense.
This article synthesizes what that position means for cloud-first companies — both large and small — and outlines a practical and prioritized roadmap for 2025–2026.
What’s behind the rising pressure
1) Data as a reward. In most incidents, attackers seek to steal and monetize information (PII, credentials, intellectual property). Extortion and ransomware account for more than half of cases with identified motivation. The “blackout” is often the megaphone of the intrusion; the real impact comes afterward, with and fines.
2) Identity, the entry point. More than 97% of identity attacks still focus on passwords (spray/brute force) and stolen credentials by infostealers and leaks. Today, many adversaries no longer force the door: they just log in.
3) Critical services, lucrative for attackers. Healthcare, local governments, education, and transportation remain targets: immediate social impact, legacy technology, and limited response resources. Ransomware groups know this and pressure with countdown clocks.
4) Smarter nation-states. While common cybercrime continues to lead volume, state actors expand their activity with espionage and influence campaigns and, sometimes, profit motives. The use of criminal infrastructure to cover tracks is growing.
5) AI as a multiplier. Attackers use AI to automate phishing, refine social engineering, identify vulnerabilities earlier, and generate adaptive malware. Defense relies on AI to detect patterns across large volumes of signals and react proactively.
What it means for a cloud-first organization
1) Prioritize phishing-resistant MFA (and clean up weak methods)
- Enforce phishing-resistant MFA on all accounts: human, privileged, service (workloads), automation, and applications.
- Remove fragile methods (SMS, reusable OTPs by default), and adopt FIDO2/WebAuthn, hardware tokens, or passkeys.
- Apply conditional policies (location, device, risk) and automated review of anomalous sessions.
Expected outcome: you’ll block >99% of unauthorized access due to stolen credentials and slow lateral movement early.
2) Seal exposed areas (and keep them sealed)
- Create a continuous inventory of exposed assets (web applications, remote services, management consoles) with quick patching.
- Position control panels and blueprints behind privileged access (PAM) and bastions; avoid default public access.
- For SaaS, disable unnecessary surfaces (legacy or open APIs) and use SCIM/Just-in-Time provisioning with automatic deactivation.
3) Truly implement Zero Trust (not just a slogan)
- Least privilege and segmentation: define blast radius by team, app, and pipeline.
- Function segregation and approvals for critical operations (KMS, IAM, networks, infrastructure).
- Centralized secrets management (vault), automatic rotation, and avoid secrets in repositories/CI.
4) Detection and response that holds up at Monday 9:00 AM
- Unify telemetry (endpoint, identity, network, cloud) into a data lake or SIEM with behavior-based rules (not just signatures).
- Prepare a tested response plan: isolate, revoke, contain, restore from immutable/disconnected copies, and notify.
- Conduct gamedays quarterly (ransom, exfiltration, provider outage, identity abuse) and measure TTR.
5) Email and web: where everything still enters
- Strengthen malware/phishing filters and add containment for browsing/downloads for risky roles.
- Deploy DMARC/DKIM/SPF with progressive reject to reduce spoofing.
- Monitor consent-phishing (unauthorized OAuth approvals) with App Governance and periodic reviews.
6) Cloud and multi-cloud resilience
- Backups with immutability and air-gap (locked objects, legal retention, recovery accounts).
- Design multi-region architectures with realistic RPO/RTO (not everything needs active-active, but critical systems do).
- Maintain emergency accounts and access outside the same failure domain (break-glass accounts with MFA, alternative monitoring dashboards).
- Conduct restoration tests with time objectives (a mere “we have backups” isn’t enough).
7) Providers, supply chain, and SaaS
- Request SBOM, hardening controls, and response plans from your providers.
- Include cyber-resilience clauses and audits; define incident notification and metrics (uptime, MTTR).
- Avoid security lock-in: portable policies and controls across clouds, to move workloads without costly redesigns.
Priorities by company size
SMBs with small teams
- Phishing-resistant MFA everywhere.
- Secure email + basic immutable backups (SaaS and endpoint).
- Inventory + patching “for what faces the internet”.
- MDR/MSSP provider to cover 24/7 with simple playbooks.
Medium and large companies
- Identity-first (MFA, CA, application governance, workload identities).
- Data-first (classification, basic DLP, encryption with their own KMS, least privilege).
- Detection and response (SIEM/SOAR, threat hunters, TTR/dwell time KPIs).
- Resilience (immutable backups, multi-region, tested runbooks).
- Governance and third parties (contracts, audits, continuity).
Metrics that matter to the board
- % of accounts with phishing-resistant MFA (human and service).
- Time to patch for critical exposed assets (median and 95th percentile).
- % of verified backups (successful restorations in tests and production).
- TTR (Time-to-Remediate) and dwell time per incident type.
- Telemetry coverage (identity, endpoint, network, cloud) and false positives.
- SaaS exposure (high-risk apps, unauthorized OAuth, public links).
Quick frequently asked questions for cloud teams
What’s the biggest “quick win” right now?
Phishing-resistant MFA for all identities (including non-human) and removing default SMS/OTP. This drastically reduces unauthorized access and session fraud.
How do I prepare my tenant against infostealers and token theft?
Implement re-authentication for context changes, invalidate tokens during incidents, strengthen browsers, and deploy EDR with rules for anomalous activity (browser to PowerShell/mshta, process injections).
Does multicloud improve security?
It offers continuity options and sovereignty if designed with portable controls (identity, logging, backups). Without governance, multiplying clouds just increases attack surfaces.
Is defensive AI mature?
For detection and prioritization, yes: it reduces analysis time and elevates the signal over noise. Keep human-in-the-loop for response decisions and ensure explainability for audits.
Summary
- Spain is in the top 5 in Europe for cyberattack frequency in 2025.
- Money — not espionage — drives most incidents; identity is the preferred avenue, and AI accelerates both sides.
- For cloud-first organizations, clear priorities are: phishing-resistant MFA, closing exposure, real Zero Trust, unified detection and response, immutable backups, and multi-region resilience with tested runbooks.
- Success is measured not by “tool count” but by TTR, dwell time, timely patches, deployed MFA, and verified restores.
The difference between a scare and a crisis is in preparation: what’s designed, automated, and rehearsed before the next Monday at 9:00.
Context source: Microsoft Digital Defense Report 2025 (global trends July 2024–June 2025: economic motivation, pressure on critical services, rise of infostealers, focus on passwords, MFA effectiveness, AI’s dual role, and nation-state activity). Full Microsoft report.
via: Cybersecurity news