In a world where a DNS outage can tank sales, interrupt a company’s email, or ruin the launch of a campaign, NSLookup.Network arrives with a simple promise: fast and reliable DNS responses, no terminal required, with a focus on privacy. The platform — free and designed for network engineers, DevOps teams, system administrators, and digital marketing professionals — executes each query via DNS over HTTPS (DoH), normalizes the query, maintains a timestamped history, and highlights the authoritative source of the data so anyone can act with confidence.
The core idea is to democratize “enterprise-level” DNS intelligence: whether an editor needs to validate record propagation, an IT team wants to troubleshoot email issues, or an agency analyzes a domain’s infrastructure, the service offers direct resolutions against authoritative servers and provides shareable links with the results. No installation required.
What’s added compared to the traditional “nslookup”
The nslookup command — present across Windows, macOS, and Linux — remains a classic. But NSLookup.Network replicates its capabilities through a web interface and adds value for collaborative work:
- DoH by default: each query is encrypted, protecting local resolvers and internal tools.
- “Cached vs. live” views: the platform accelerates repeated queries with cache and allows forcing live data to confirm real changes.
- Permalinks: each lookup generates a shareable URL, useful for tickets, post-mortems, or audits.
- Timestamped history: every response is sealed in time, essential for justifying propagation windows or evidencing record changes.
- Visible authoritative source: emphasizes which authoritative server responded, minimizing doubts in cases of desynchronization or split-horizon DNS.
Record coverage and use cases
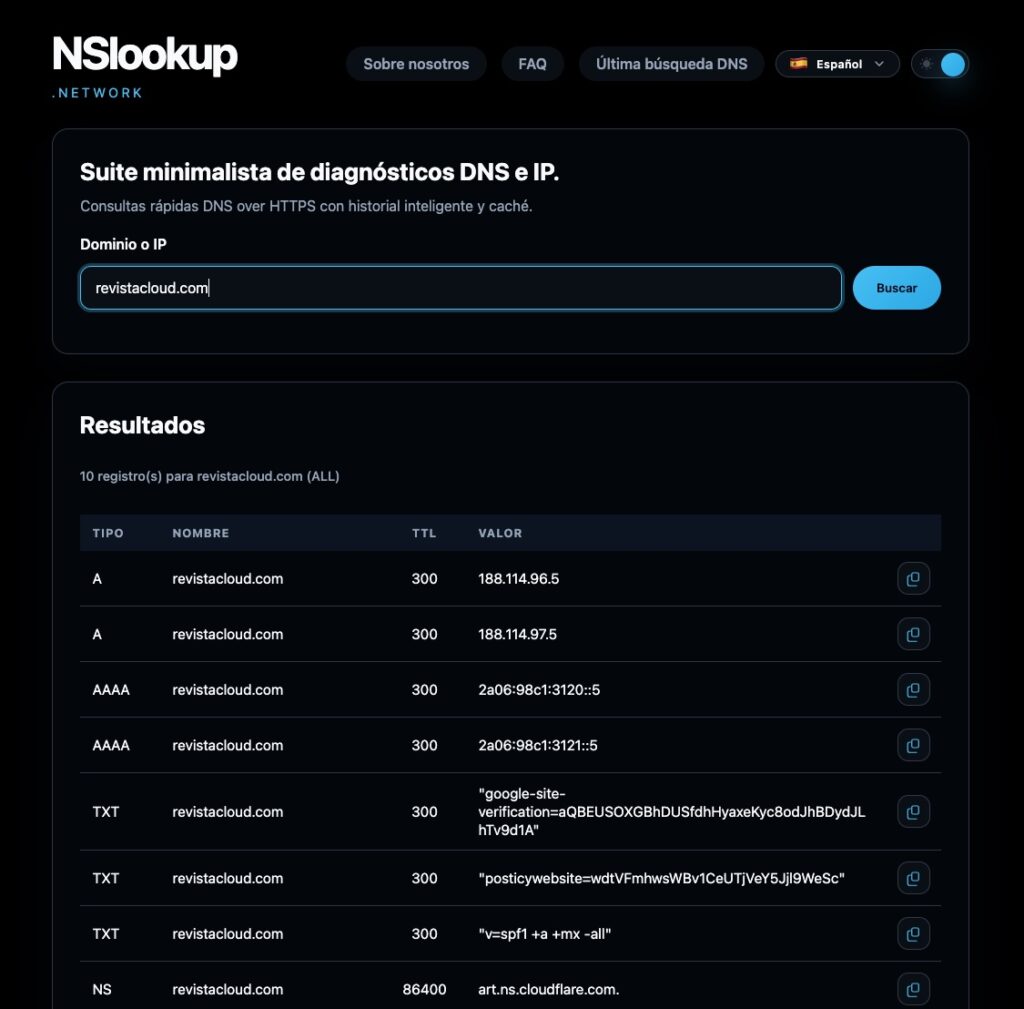
The tool supports the essential record types for 2025 operations:
- A / AAAA: IPv4 and IPv6 addresses resolving the website’s frontend.
- MX: Mail exchangers routing incoming email.
- TXT: SPF, DKIM, DMARC, and verification tags (providers, clouds, search engines).
- NS: nameserver delegations defining domain authority.
- SOA: Start of Authority with serial, refresh, and retry — critical during migrations.
- PTR: reverse DNS for IP reputation and email validation.
You can query a single record type or request “all records” to compare responses in one view. Operationally, it’s useful for:
- Validating DNS migrations: testing new NS records, reviewing the SOA serial, and estimating propagation based on TTL.
- Troubleshooting email issues: confirming provider’s MX, reviewing SPF/DKIM/DMARC, and performing reverse PTR lookups on IPs.
- Auditing infrastructure changes: detecting delegation modifications, new IPs, or added TXT records in your domain or competitors’.
- Ensuring launch readiness: before campaigns, verifying resolution points to the correct backend and that certificates/hosts won’t trigger SSL warnings due to outdated caches.
Why querying authoritative sources matters (not just any resolver)
In DNS, the ultimate truth resides with authoritative servers. If these are out of sync or misconfigured, users may see stale IPs, broken email, or SSL alerts. NSLookup.Network gets the response directly from those sources, ensuring what’s visible after propagation is what Internet users will see.
For teams dealing with intermittent issues, this distinction saves hours: a recursive resolver might serve cached data due to TTL; the authoritative source reveals the true state of the domain.
Recommended workflow
- Enter domain or IP and select record type (or “All”).
- Compare cache vs. live to detect recent changes.
- Check TTL and SOA serial to estimate propagation windows.
- Repeat from another network if regional caching or CDN are suspected.
- Share the permalink in the ticket or changelog and record the verification time.
For nameserver migrations, it’s recommended to test NS and SOA before modifying glue records in your registrar. When troubleshooting email issues, validate SPF/DKIM/DMARC and MX records against provider documentation.
Who it’s for
- Network engineers and DevOps needing reliable, tracable visibility without relying on a jump host.
- System administrators troubleshooting issues across multiple teams, requiring verifiable links for coordination.
- Digital marketing / technical SEO validating domain propagation, campaign subdomains, or TXT verifications without terminal access.
- Consultants and agencies providing independent evidence to clients and NOC/SOC colleagues.
Service philosophy: privacy and collaboration
The team behind NSLookup.Network defines it as a free community resource: DoH for privacy, smart caching to speed up repeats, an option for live confirmation when needed, and timestamped history for documentation. They also invite collaboration: ideas for custom monitoring flows and product improvements are welcome.
Key DNS quality signals to watch (and that NSLookup.Network exposes)
- SOA serial: Does it increase with each change? Does it match across authoritative servers?
- Consistent TTLs: Are there very high TTLs hindering urgent updates?
- NS delegations: Do they point to active and synchronized nameservers?
- Email TXT records: Correct SPF mechanisms, valid DKIM, and appropriate DMARC policies.
- PTRs: Does the reverse DNS of sending IPs resolve to the expected FQDN?
What it does NOT do (and it’s useful to clarify)
NSLookup.Network does not replace 24/7 monitoring or a change management system. It does not modify records — it views and documents. For automation, alerts, or probes from multiple regions, integration with other tools will be necessary; here, the value lies in quick responses and frictionless sharing of evidence.
Conclusion
With NSLookup.Network, tasks that previously required VPN access, jumping to a bastion host, and running commands can now be done within seconds and via shareable link. For distributed teams and stakeholders without technical skills, this simple change accelerates diagnostics, reduces misunderstandings, and improves documentation hygiene during deployments or migrations. As a free service focused on DoH, source authority, and historical records, it adds a layer of confidence many users missed in web DNS utilities.
Frequently Asked Questions
How to verify a nameserver migration step-by-step (NS and SOA) with an online tool?
Look up the domain on NSLookup.Network, check NS and SOA in “live” mode, note the serial and TTL. Repeat after making changes at your registrar and compare serial/TTL. Share the permalink in the ticket to document before-and-after states.
How to diagnose email delivery issues with DNS records without terminal access?
Verify MX (should point to your provider), review SPF/DKIM/DMARC in TXT records, and check PTR of sending IPs. NSLookup.Network displays authoritative servers and TTL. If a policy change still fails, use live data confirmation to verify propagation.
How to tell if the data I see is final or from an intermediate cache?
Compare cache vs. live. The live view queries authoritative servers via DoH; if they differ, wait for TTL or consult from another network. The SOA serial helps confirm the change is published at source.
What records should I check to avoid SSL warnings or inconsistent resolutions after deployment?
Check A/AAAA for correct IP, CNAME if applicable, and verify NS and SOA to rule out desynchronized authoritative data. If using CDN, repeat the live lookup and check TTL to estimate when users will see the change.

