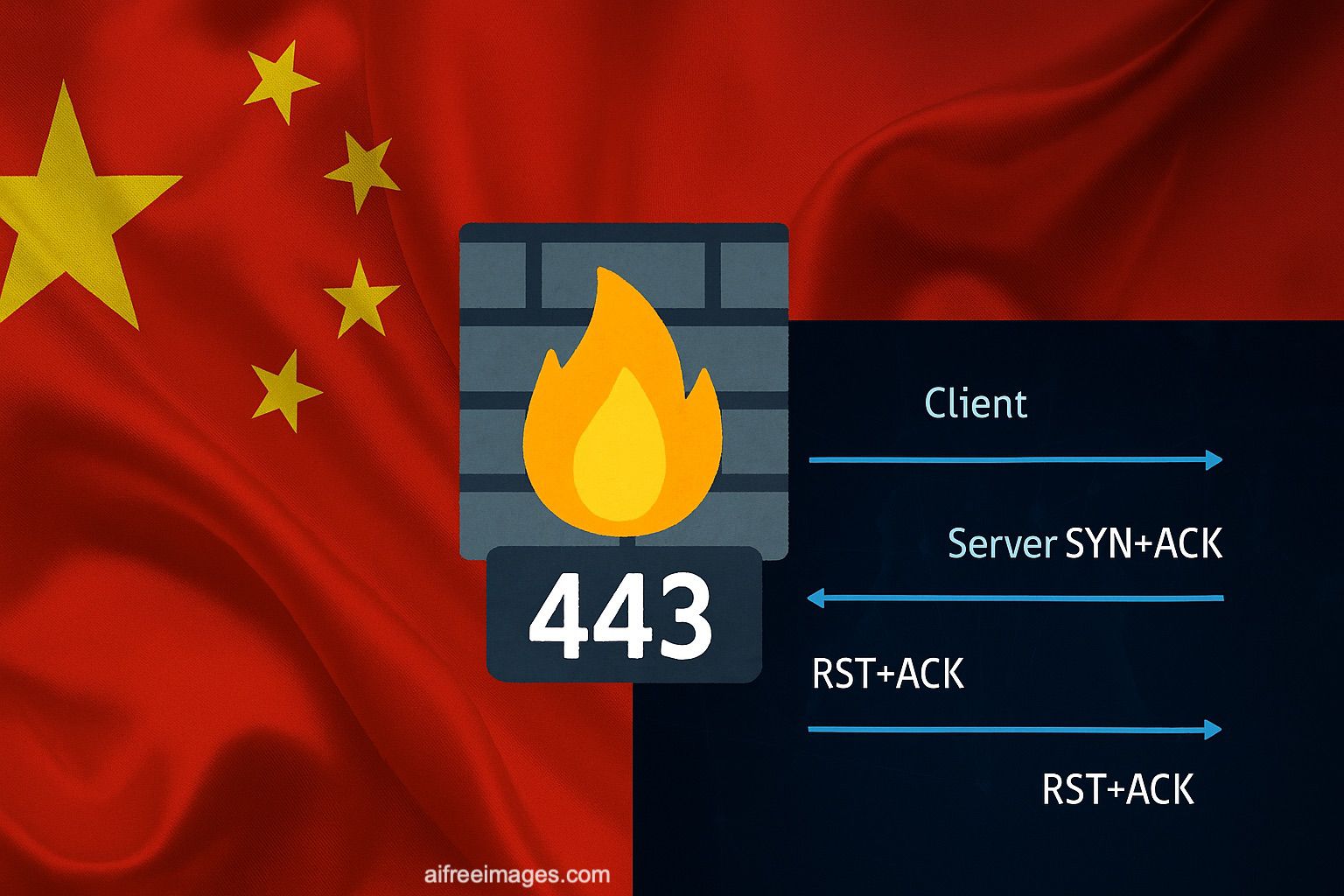
On August 20, 2025, at midnight in Beijing, millions of Chinese internet users were surprised by a brief yet significant incident: for 74 minutes, the Great Firewall of China (GFW) completely and indiscriminately blocked TCP port 443, the most widely used port worldwide for HTTPS traffic—encrypted communications that underpin the modern digital economy.
This event, documented by GFW Report, an independent group monitoring digital censorship in China, involved the massive injection of counterfeit TCP RST+ACK packets. These packets, generated by GFW systems, forced the disconnection of any secure connection attempts, whether from domestic users accessing external sites or from foreign servers responding to Chinese clients.
The result was a selective digital blackout that, although lasting just over an hour, demonstrated Beijing’s ability to instantly and voluntarily isolate its population from the rest of the world.
A technical failure or a deliberate test?
The incident began at 00:34 Beijing time and ended at 01:48, when HTTPS traffic resumed normally. However, analyses leave an open question: was this a technical malfunction caused by misconfigured equipment, or a deliberate experiment by the Chinese government to assess its network’s resilience to full isolation?
Investigators note that the injected packets do not match the usual digital signatures of known GFW devices. This detail suggests two possible explanations:
That it was a new censorship device still in testing.
That an existing device was operating in an undocumented or faulty mode.
Regardless, the impact was clear: millions of secure connections were interrupted, affecting domestic users, multinational companies based in China, and global cloud services.
What is port 443 and why is it vital?
In the internet, data travels through numeric ports serving as gateways for various applications. Port 443 is the global standard for HTTPS traffic—secure connections using digital certificates to encrypt client-server communications.
Every time a user logs into an online bank, makes a purchase on Amazon, checks email on Gmail, or connects via platforms like Zoom or Teams, it’s through port 443. Blocking it essentially halts the backbone of the global digital economy.
While HTTPS can technically be configured on other ports, most services operate on port 443. Therefore, shutting down this “door” caused an immediate and widespread disruption.
The technical mechanism: injection of fake packets
To understand what happened, it’s helpful to explain the concept of RST+ACK packet injection in simple terms.
In a normal TCP connection, two devices (client and server) exchange initial messages known as a three-way handshake:
The client sends a SYN to start a connection.
The server responds with SYN+ACK to confirm.
The client replies with ACK, and the connection is established.
What the GFW did was intercept these messages and insert a counterfeit RST+ACK packet. This packet instructs both ends to immediately close the connection, as if either side had decided to abort the communication.
The result: the user’s browser believes the foreign server rejected the connection, while the server thinks the client has hung up. The connection is never established.
Additionally, in this incident, the fake packets showed incremental variations in technical parameters (like TCP window size or TTL), not seen in previous GFW injections. This suggests the attack came from a new or modified device—supporting the hypothesis of a controlled test.
Impact on users and businesses
For over an hour, users inside China couldn’t securely access global services:
Encrypted email platforms (like ProtonMail or Gmail).
Video conferencing and remote work tools (Zoom, Teams, Slack).
E-commerce and electronic payments (Amazon, Alipay International, PayPal).
VPN services relying on HTTPS tunnels.
Multinational companies with operations in China had to halt video calls, file transfers, and data synchronization with headquarters abroad. Although brief, this incident highlighted the fragility of global interconnection when China’s sizable infrastructure unilaterally cuts its link to the outside world.
A test of digital sovereignty
International analysts see this episode within a broader geopolitical context: China’s strategy of technological sovereignty.
Under Xi Jinping, China has promoted the idea of an “internet with Chinese characteristics”—controlled domestically and less dependent on foreign providers. The August 2025 blackout can be viewed as a test of digital isolation, simulating how the infrastructure might respond if disconnected from the global network.
In a time of tensions with the U.S., the EU, and neighboring Indo-Pacific countries, such maneuvers send a clear message: China can disconnect at will and force its population and businesses to rely solely on domestic services.
Precedents of the Great Firewall
The GFW has a history of digital disruption:
In 2015, the “Grand Canyon” attack used GFW infrastructure to inject malicious code into connections and launch DDoS attacks against GitHub.
In 2019, it temporarily blocked GitHub, causing discomfort among the local tech community.
In 2021 and 2022, censorship intensified against encrypted messaging apps like Signal and WhatsApp.
However, the 2025 event marks a significant leap: it wasn’t targeting a specific service but a total blockade of HTTPS infrastructure.
Global consequences
Such a cut extends beyond China’s borders. Digital supply chains, which rely on constant communication between servers in different countries, were also impacted. Logistics, financial, and tech companies with clients or suppliers in China faced unexpected disruptions.
In terms of international trust, episodes like this cast doubt on China’s reliability as a digital partner. If a country can cut its connection at will, the risks for global trade, foreign investment, and cybersecurity grow considerably.
Future scenarios
This incident opens several possible futures:
Isolation test: Beijing tested its ability to digitally disconnect and measure the consequences.
Configuration error: A new GFW device malfunctioned unexpectedly.
Geopolitical signal: The blackout was a reminder that China can use its digital infrastructure as a tool of pressure.
In any case, it demonstrates that the internet isn’t as decentralized as often thought — control of a few critical points can halt the flow of data worldwide within minutes.