An analysis of over 19 billion leaked passwords reveals a concerning reality: 94% are predictable, weak, or reused.
In the age of Artificial Intelligence, edge computing, and quantum computing, millions of people still protect their digital accounts with passwords like “123456,” “password,” or their own name. This is evidenced by the most comprehensive analysis to date of leaked passwords from global cyber incidents that occurred between 2024 and 2025.
The study reveals that only 6% of the analyzed passwords are unique, while the vast majority fall into common, easy-to-guess patterns that are highly vulnerable to automated attacks.
Insecure Passwords in 2025: Key Conclusions
- 42% of passwords are between 8 and 10 characters long, with eight being the most commonly used length.
- 27% consist only of lowercase letters and numbers.
- Only 19% incorporate uppercase letters, lowercase letters, numbers, and symbols.
- “123456” remains the most common password, present in over 338 million accounts.
- Common words like “admin”, “password”, proper names (especially “Ana”), and positive terms like “love,” “sun,” or “dream” are extremely popular.
- Offensive and vulgar words, as well as pop culture references like “Mario,” “Batman,” or “Elsa,” are also notable.
Why is it a Critical Problem?
In terms of cybersecurity, weak passwords are open doors. Brute-force attacks and credential stuffing—where cybercriminals try millions of combinations extracted from leaks—are becoming increasingly sophisticated. Even a success rate of 0.2% can lead to thousands of compromised accounts.
Moreover, these credentials are sold and reused in chains of more complex attacks that include:
- Access to bank accounts and financial services.
- Identity theft and digital fraud.
- Lateral access to corporate infrastructures.
- Deployment of ransomware or custom malware.
Most Common Patterns in 2025
1. Default Passwords and Keyboard Sequences
Despite warnings, “123456,” “admin,” and “qwerty” remain the most used. Default passwords set by devices like routers or mobile phones often go unchanged after installation.
2. Use of Names, Dates, and Common Words
Proper names, especially “Ana,” appear in almost 1% of all passwords. Other frequent components include words like “banana,” “monday,” “god,” “pizza,” “freedom,” or “summer.”
3. Offensive Combinations
Interestingly, millions of passwords include words like “fuck,” “shit,” “dick,” or “bitch,” used as a form of personalization but common in attack dictionaries.
4. Simple Passwords and Poor Structures
A high percentage of passwords lack symbols and uppercase letters. Only 19% achieve a minimum complexity, far from the standard recommended by security experts.
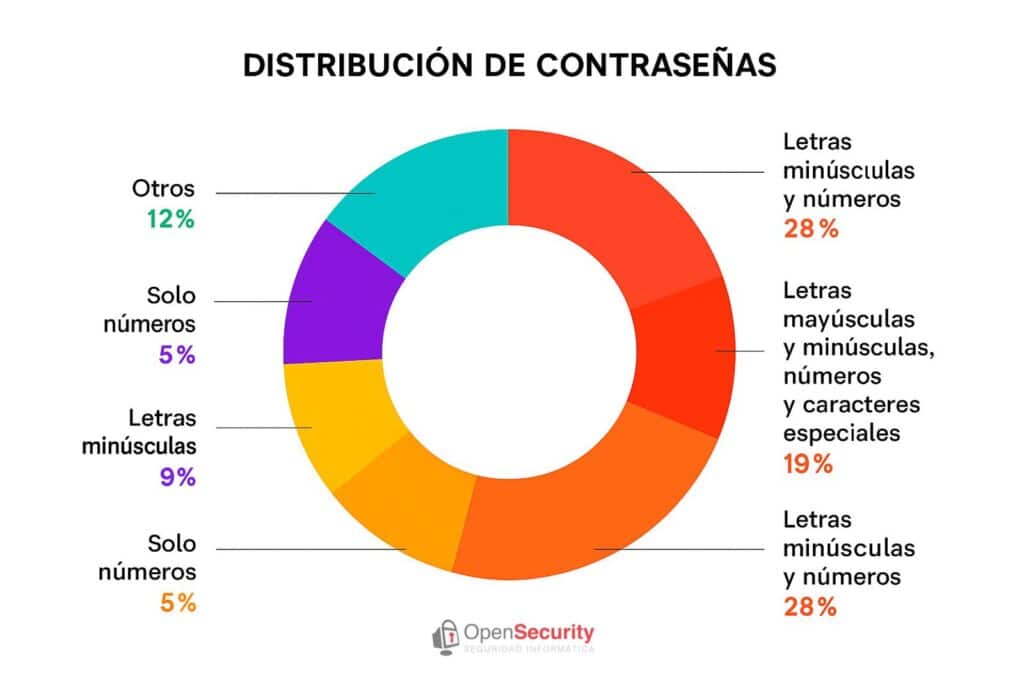
Distribution of Password Composition
A visualization based on the analysis shows that:
- 28% use lowercase letters and numbers.
- 28% mix uppercase and lowercase letters with numbers.
- 19% include letters, numbers, and symbols.
- The remainder is divided among numeric-only passwords, lowercase letters only, or other patterns.
(A complete infographic of the distribution by password type is available.)
Key Recommendations for Users and Organizations
For Users:
- Use long passwords (at least 12 characters) and a variety of characters.
- Never reuse passwords between different services.
- Avoid using your name, dates, or recognizable words.
- Enable two-factor authentication (2FA) whenever possible.
- Use a trustworthy password manager.
For Organizations:
- Implement robust password policies with periodic expiration.
- Apply proactive detection of leaked credentials.
- Monitor access and anomalous behaviors.
- Educate and train staff on good cybersecurity hygiene practices.
- Implement tools to protect against credential stuffing attacks.
Conclusion
The report makes it clear that, despite technological advancements, the security of millions of accounts still relies on weak passwords. In a context where attacks are automated and global, continuing to use “123456” is like leaving the door open to attackers.
Investing five minutes in creating a strong password can save you months of headaches, financial losses, and reputational risks.
Source: Security News

