Experts warn that the uptick in activity could signal an impending campaign of attacks or the imminent exploitation of a new vulnerability.
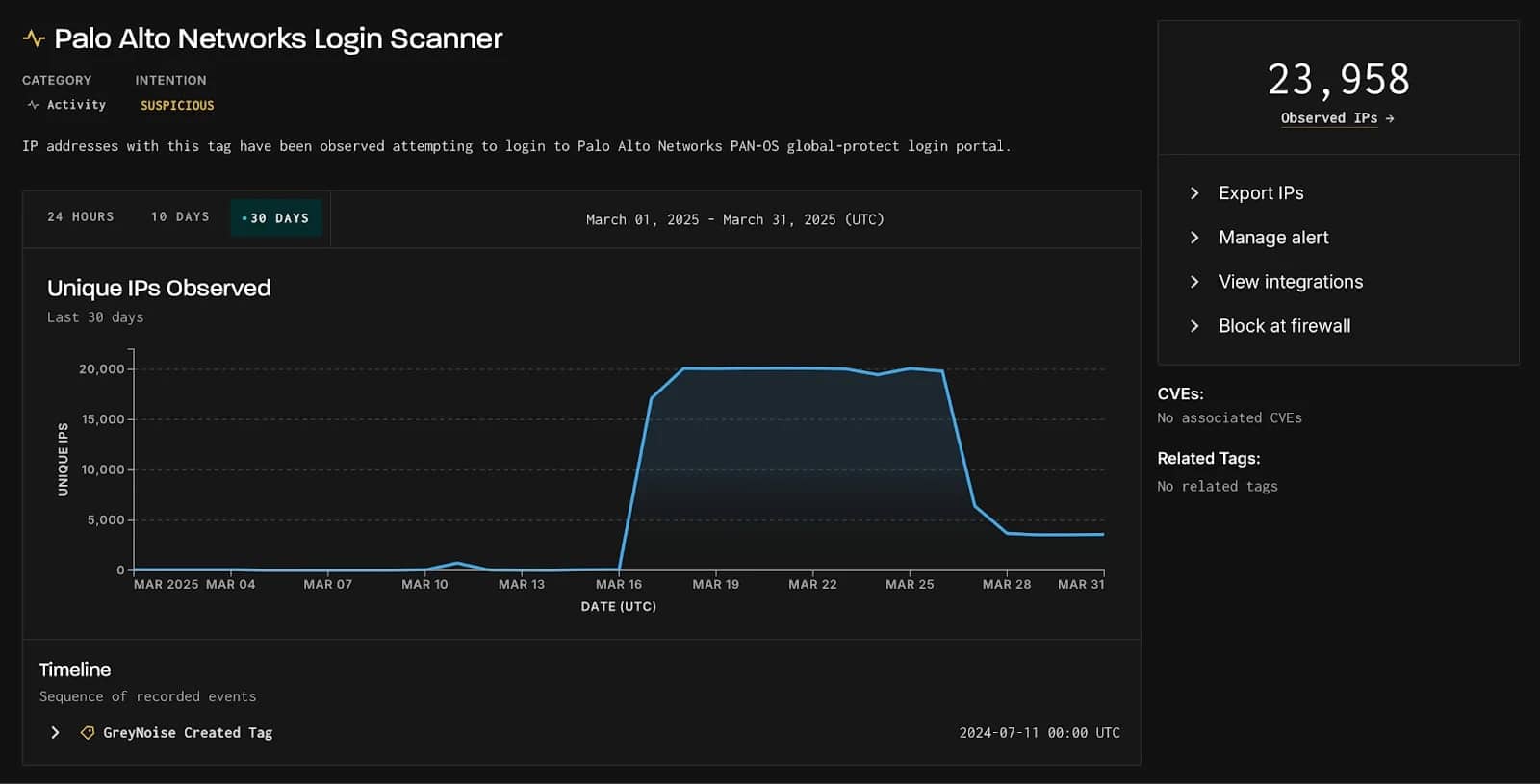
A massive scanning campaign has raised alarms in the cybersecurity community after an unusual spike in attempts to access login portals for GlobalProtect, the enterprise VPN solution from Palo Alto Networks. According to researchers from GreyNoise, more than 24,000 unique IP addresses were involved in this suspicious activity during March 2025.
Large-Scale and Persistent Scans
The highest peak was recorded on March 17, with 20,000 active IPs in a single day, a number that sustained until the 26th. GreyNoise classified 23,800 of these IPs as “suspicious” and 154 as “malicious”, indicating a clear intention of reconnaissance before a possible attack.
The majority of the connections originated from the United States and Canada, although the targeted systems include organizations from various regions around the world, with a particularly high concentration in U.S. servers exposed to the Internet.
“Over the last 18 to 24 months, we have identified a clear pattern: reconnaissance campaigns against specific technologies that, weeks later, precede the disclosure of new vulnerabilities,” explained Bob Rudis, Vice President of Data Science at GreyNoise.
Possible Prelude to a New Vulnerability
Although no specific flaw in GlobalProtect has been confirmed, the observed behavior is reminiscent of previous campaigns where attackers map vulnerable assets to exploit future security gaps, including those that remain unknown (zero-days).
GreyNoise also noted a coincidence with parallel activity recorded on March 26, involving a PAN-OS scanner that included 2,580 IPs, which could be part of the same operation or share common infrastructure.
Researchers compare this pattern to the espionage campaign ArcaneDoor, revealed by Cisco Talos in 2024, which also targeted perimeter devices and corporate networks.
Urgent Recommendations for Administrators
Although Palo Alto Networks has not yet confirmed any exploited vulnerabilities in this campaign, they have issued a brief statement indicating that their teams are “actively monitoring the situation” and that “the security of customers is their top priority”.
In the meantime, GreyNoise recommends that system administrators using GlobalProtect do the following:
- Audit logs from mid-March to detect anomalous scans or suspicious access attempts.
- Look for signs of compromise in their perimeter infrastructures.
- Strengthen the configuration of login portals, including the use of multi-factor authentication and restrictive access policies.
- Update to the latest version of PAN-OS, following the manufacturer’s best practices.
- Block known malicious IPs provided by GreyNoise.
⚠️ Conclusion
The surge of scans against GlobalProtect does not appear to be an isolated incident but part of a repeated pattern of pre-exploitation surveillance. Although there is currently no concrete evidence of an ongoing attack, organizations must take a proactive stance and strengthen their security controls before it’s too late.
References: Bleeping Computer and GreyNoise

