Here’s the translation of your text into American English:
Many small and medium-sized enterprises (SMEs) erroneously believe that they are not attractive targets for cybercriminals, thinking that these criminals prefer to attack large corporations with a higher volume of data. However, the reality is that SMEs are often more vulnerable targets due to their less robust security systems. The information they store can be valuable and used for various criminal purposes.
How do cybercriminals monetize stolen data?
The theft of business information is one of the most lucrative practices within cybercrime. Cybercriminals can gain access to confidential data in different ways, such as through phishing, spyware, or ransomware attacks. Once in their possession, stolen data can be used for:
💰 Financial Gain
Cybercriminals seek to monetize stolen information by selling data on black markets. On the dark web, they can trade access credentials, banking information, and other sensitive data from businesses and customers.
Additionally, financial and personal information can be exploited to commit fraud, carry out illegal transfers, or even extort victims in exchange for not disclosing the stolen data.
🆔 Identity Theft
The theft of credentials is one of the most common strategies in cyberattacks. With access to email accounts, social media, or business platforms, attackers can impersonate the victim, compromising their reputation and security.
Cybercriminals can use stolen information to open bank accounts, apply for loans, or make fraudulent purchases. They can also exploit the tendency of many users to reuse passwords, facilitating access to multiple accounts with a single compromised credential.
📩 Use in Phishing and Spam Campaigns
Databases of email addresses are a valuable asset for attackers. These can be sold or used in phishing and spam campaigns, aiming to trick new victims into revealing more information or installing malware on their devices.
This type of attack can affect companies of any size and lead to financial losses or reputational damage.
🔓 Sabotage, Espionage, and Other Cyberattacks
Access to a company’s systems can allow cybercriminals to carry out more sophisticated attacks, such as:
- Business Sabotage, affecting the operation of the company by altering or deleting data.
- Industrial Espionage, leaking sensitive information to competitors or groups with specific interests.
- Ransomware Attacks, where the company’s information is encrypted, and payment is demanded for its recovery.
- Using systems as part of a botnetA botnet is a network of compromised and controlled computers, utilizing the company’s computing resources to launch DDoS attacks or mine cryptocurrencies without their knowledge.
In some cases, cybercriminals use access to small businesses as an entry point to attack larger networks, especially if these companies work with large corporations.
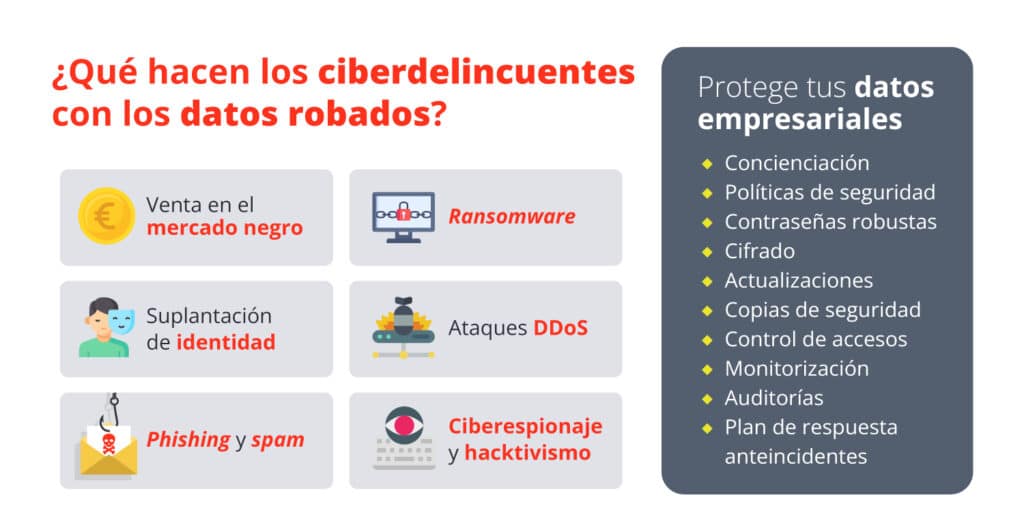
How to Protect Your Business Against Data Theft?
Given the growing risk of cyber attacks, it is essential for businesses to adopt proactive strategies to protect their information. Some of the best practices include:
🛡️ Training and Awareness in CybersecurityCybersecurity solutions are essential in today’s era
Employees are the first line of defense against cyberattacks. It’s crucial to:
✔️ Train staff to identify attempts of phishing and social engineering attacks.
✔️ Establish clear security policies, ensuring that all employees are aware of their responsibilities.
🔑 Implement Secure Passwords and Multi-Factor Authentication (MFA)
To reduce the risk of unauthorized access:
✔️ Use complex passwords with uppercase, lowercase, numbers, and symbols.
✔️ Avoid reusing credentials across different accounts.
✔️ Enable two-factor authentication whenever possible.
🔒 Data and Communication Encryption
Protecting information at rest and in transit reduces the impact of breaches:
✔️ Use secure protocols (HTTPS, VPNs, end-to-end encryption).
✔️ Ensure that critical data is encrypted to prevent misuse in the event of theft.
⚙️ Software Updates and Security Patches
Cybercriminals exploit vulnerabilities in outdated software:
✔️ Keep operating systems and applications updated.
✔️ Apply security patches as soon as they are available.
📂 Regular Backups
Having updated backups is key to recovering from attacks like ransomware:
✔️ Perform automated and regular backups.
✔️ Store backups in secure and offline locations.
✔️ Test data recovery to ensure functionality.
👨💻 Access Control and Continuous Monitoring
Limiting access to business information can prevent leaks:
✔️ Implement role-based access control policies (principle of least privilege).
✔️ Use activity monitoring tools to detect suspicious access.
✔️ Conduct regular security audits to identify and correct vulnerabilities.
🛠️ Incident Response Plan
Preparing for a cyberattack can minimize its impact:
✔️ Design a contingency plan to act in case of a data breach.
✔️ Define communication protocols for notifying incidents to employees, customers, and authorities.
✔️ Simulate attacks and regularly review procedures to improve preparedness.
Conclusion: Cybersecurity is an Investment, Not an Expense
Increasingly, cybercriminals target small and medium-sized businesses, taking advantage of their security weaknesses. However, implementing appropriate protective measures can make the difference between becoming a victim of an attack or maintaining the integrity of information.
No matter the size of the business: any data can be valuable on the black market. Therefore, investing in training, security tools, and best practices is essential to prevent risks and ensure business continuity.

