Here’s the translation into American English:
A report from StrongDM reveals that Zero Trust implementation is progressing, but hybrid and multi-cloud environments hinder its effectiveness.
The adoption of the Zero Trust model has grown significantly in recent years, with 81% of companies implementing it partially or fully to enhance their cybersecurityCybersecurity solutions are essential in the digital age. However, 49% of organizations face serious challenges in managing security policies in multi-cloud infrastructures, according to a recent study by StrongDM, which surveyed 600 cybersecurity professionals in the United States.
Zero Trust: From Strategy to Necessity in Cybersecurity
The report confirms that Zero Trust has become a key priority in cloud data protection, especially with the rise of remote work and the digitization of operations. 84% of companies are applying this model in their cloud security strategy, with identity and access management (IAM) and data encryption as the primary focuses.
However, the implementation of Zero Trust is not without barriers:
- 22% of respondents cite internal resistance to adopting the model.
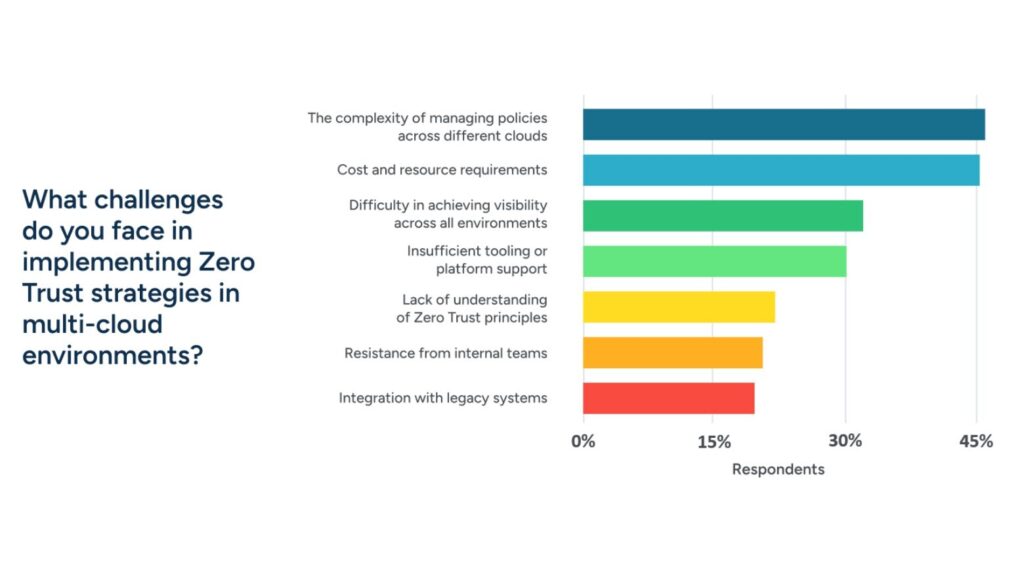
- 48% indicate that costs and lack of resources are the main obstacles.
- 57% admit that their controls over databases are minimal or non-existent, exposing sensitive information to unnecessary risks.
Multi-Cloud Infrastructures: The Major Challenge of Zero Trust
The rise of multi-cloud environments has complicated security management in companies with hybrid infrastructures. The combination of multiple cloud service providers creates fragmentation in access management and security policies, making the implementation of a unified Zero Trust strategy more challenging.
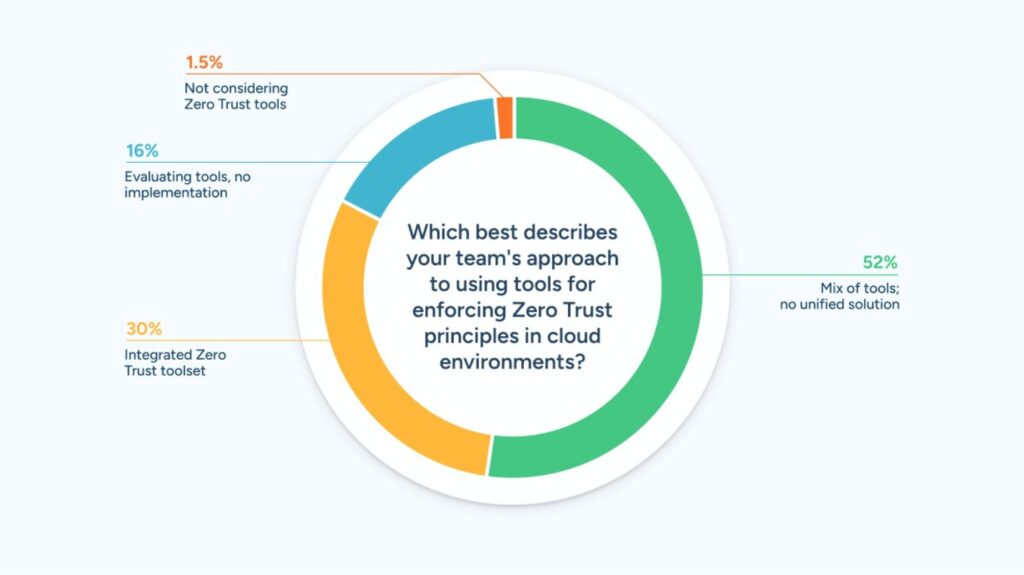
According to the report, nearly half of companies (49%) struggle to maintain consistent management of their security policies in multi-cloud infrastructures. This issue is exacerbated because:
- 52% of organizations use multiple security tools, rather than a unified solution.
- Only 30% have a centralized platform for managing Zero Trust.
- 28% continue to use the same security tools for cloud and on-premises environments, leading to inconsistencies.
Toward a More Efficient Zero Trust Implementation
The StrongDM report emphasizes that, to improve security in the cloud, companies must focus on solutions that simplify access policy management.
The most sought-after aspects by cybersecurity professionals include:
- Real-time monitoring, prioritized by 60% of respondents.
- More intuitive policy management systems, identified as essential by 45%.
Despite the challenges, the study makes it clear that Zero Trust is not just a trend but a key component of the security strategy for modern businesses. The need to protect data in increasingly decentralized environments demands more integrated and flexible approaches, where automation and centralized management will play a crucial role in the coming years.
via: Security News

